To facilitate the Power Embedded installation process, we have created this tutorial to help our customers install Power Embedded.
Prerequisites for performing the installation
As Power Embedded is a SaaS system, you will not need to guy or manage any server, application or database, you will just use the software as a service.
To set up Power Embedded in your company, we need the following prerequisites to be met before we can schedule the installation:
- An Azure user account with permission to create Fabric or Embedded capacity.
- An Azure user account with permission to create groups and application registrations in Azure AD.
- Account of an Azure user who has the “Fabric administrator” role to access the Power BI admin portal.
During the system installation meeting, which is held together with the client, we need to have a user with the permissions listed above, or someone from the customer's team with these permissions, someone that can share the screen and perform the required tasks that will be instructed.
How to create Power Embedded application in Azure AD
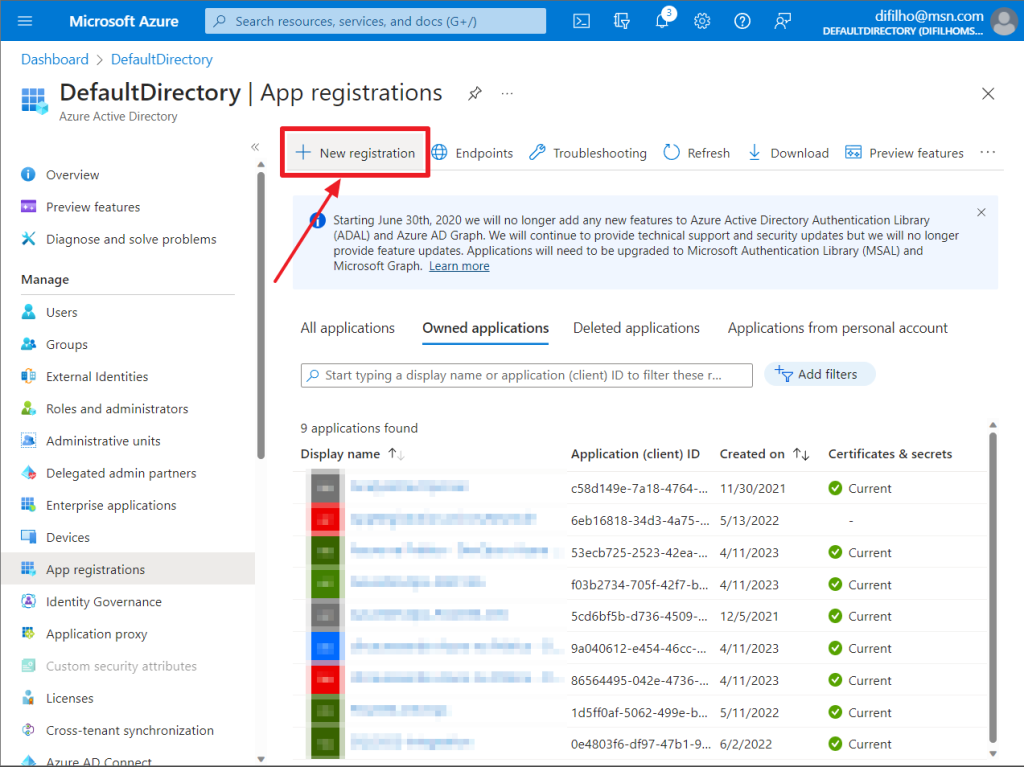
To register the application that will be used by Power Embedded, you will need to access this link here.
On the screen below, click on the “New registration” button
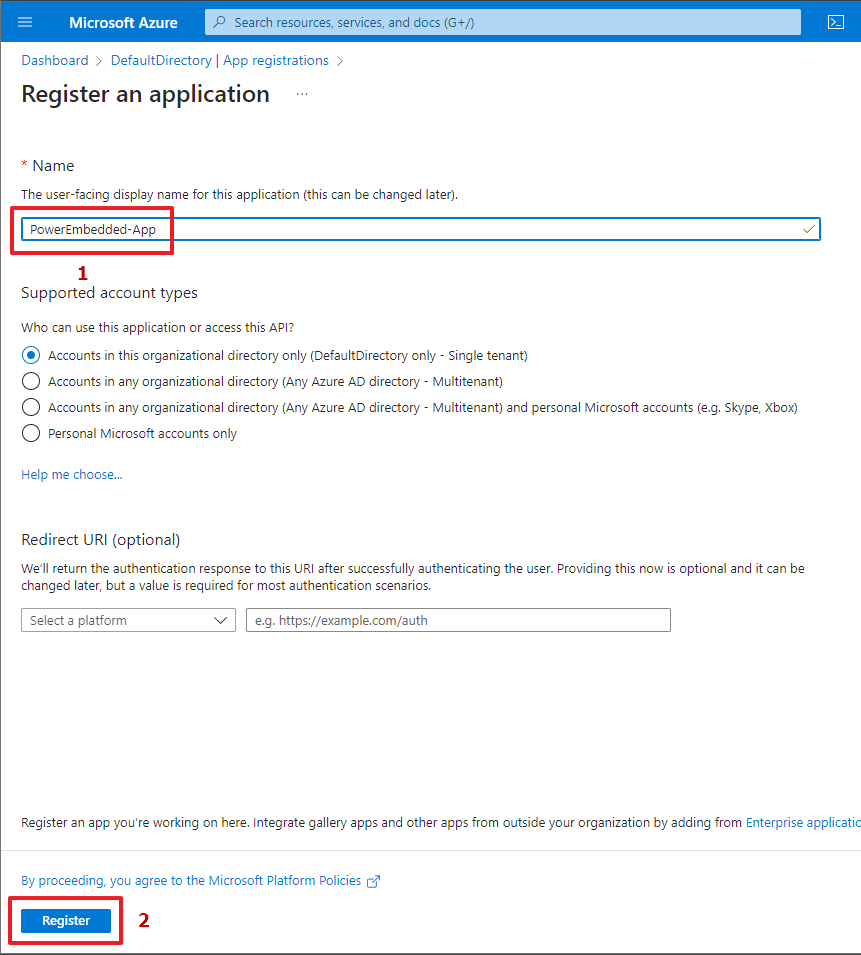
Now you will need to choose a name for the application that you will create in your Azure AD. The name is up to you.
After that, click on the “Register” button at the end of the page.
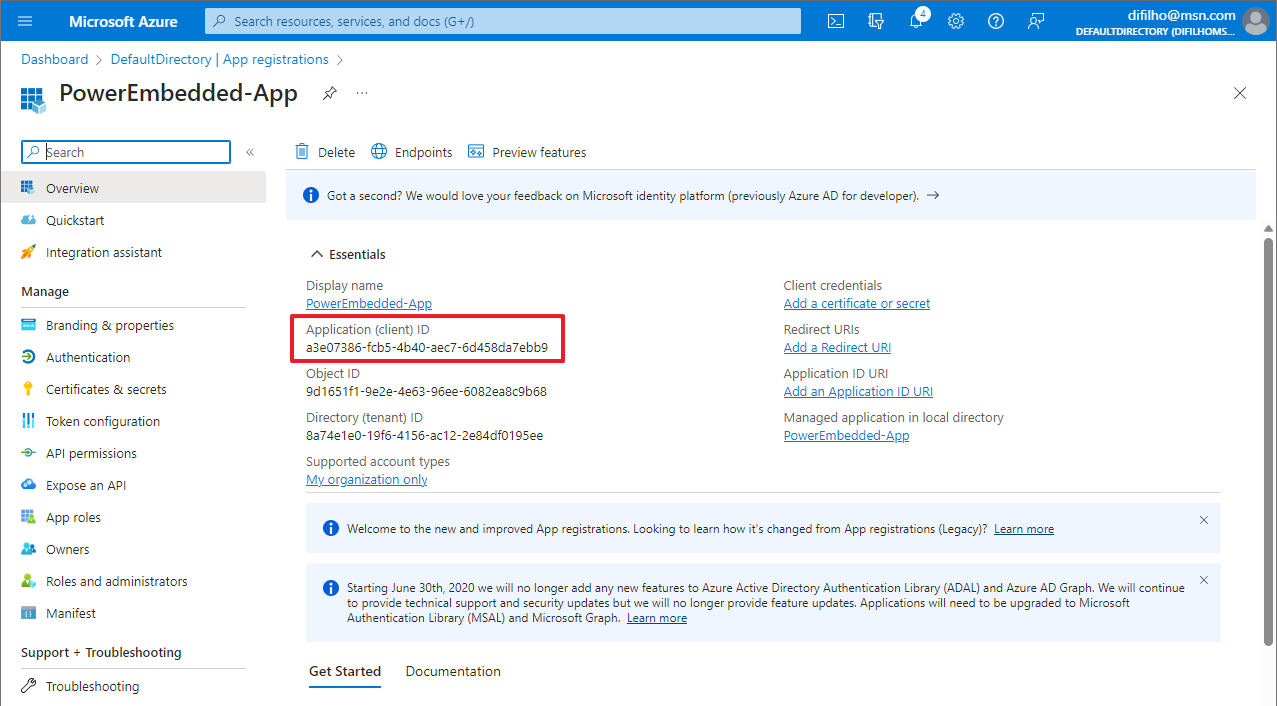
After creating this Application, you will be directed to the overview screen for that user.
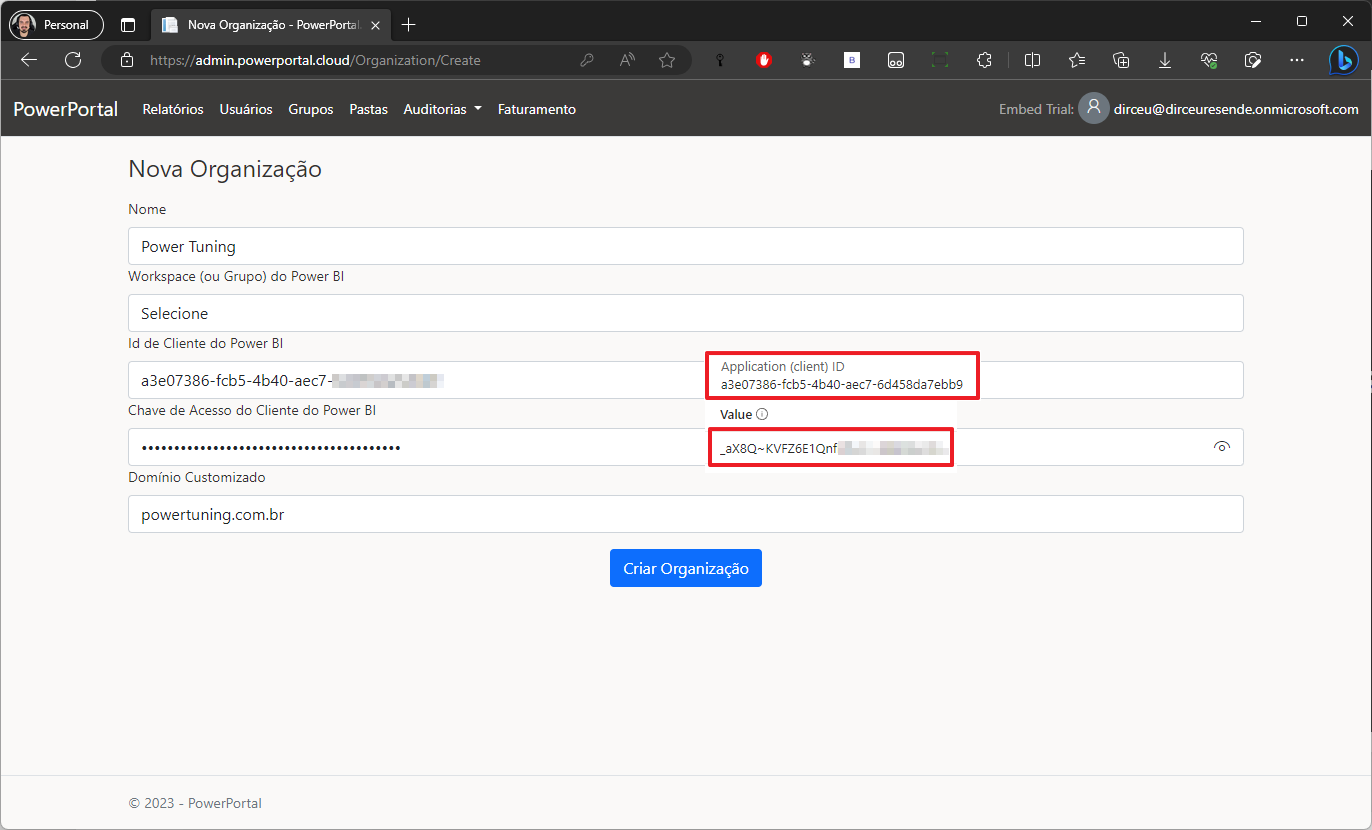
Copy the value from the “Application (client) ID” field and save it in a notepad. This key is what you will paste into the “Power BI Client Id” in the Power Embedded organization configuration.
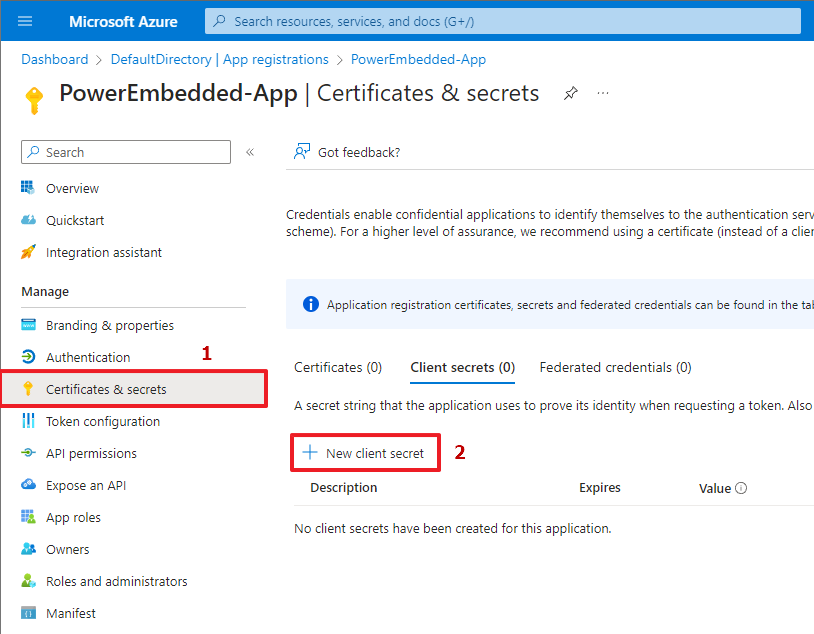
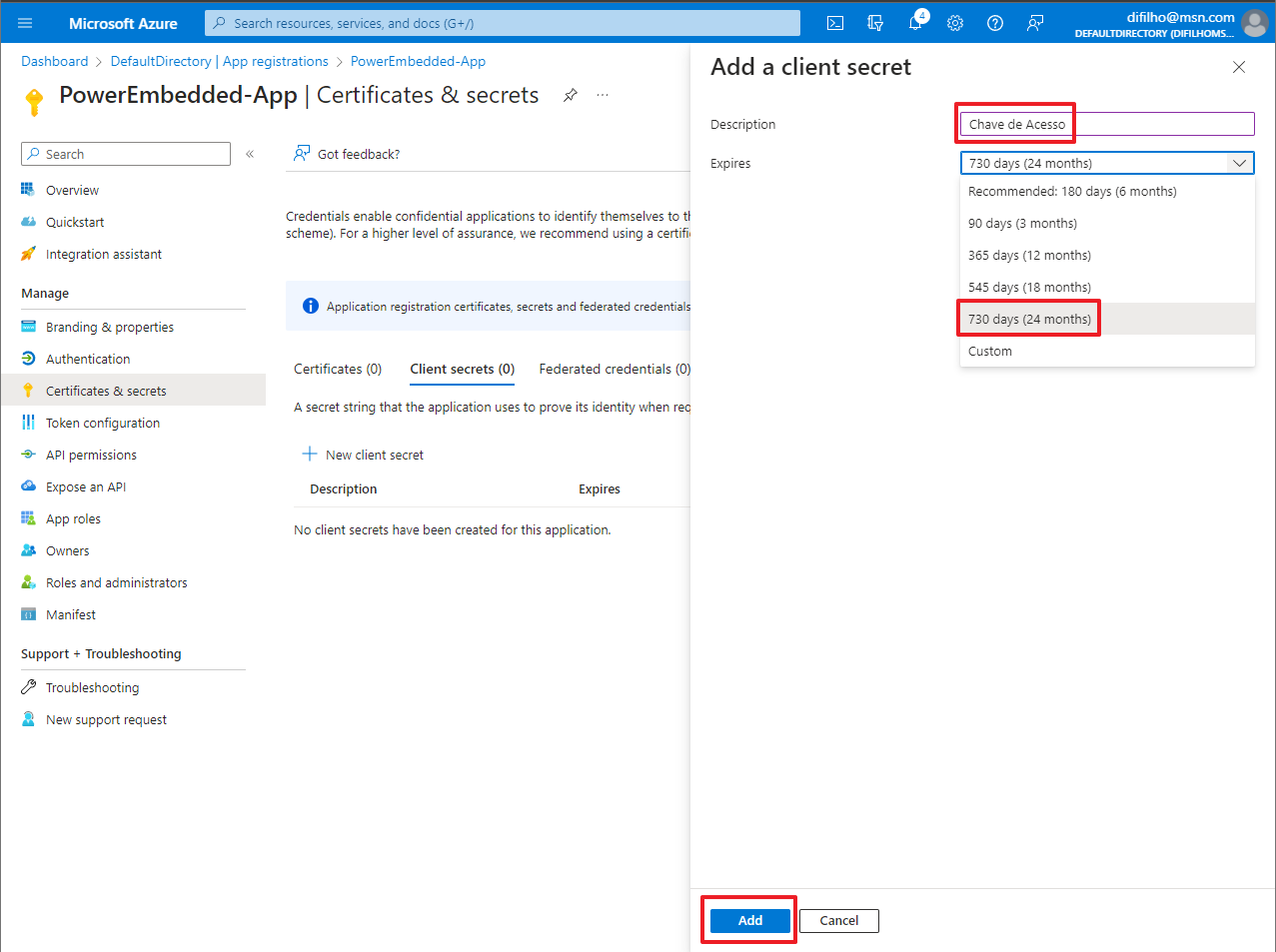
Now click on the “Certificates & secrets” option and then click on the “New client secret” button
In the new screen that opens, enter a description for this secret (as per your preference) and select the validity of this secret.
I suggest choosing 24 months so that you only need to worry about this expiration after 2 years (Yes, after the chosen period, this secret will expire and the system will STOP working. You will need to generate a new secret and update it in Power Embedded).
Now click on the “Add” button at the bottom of the page.
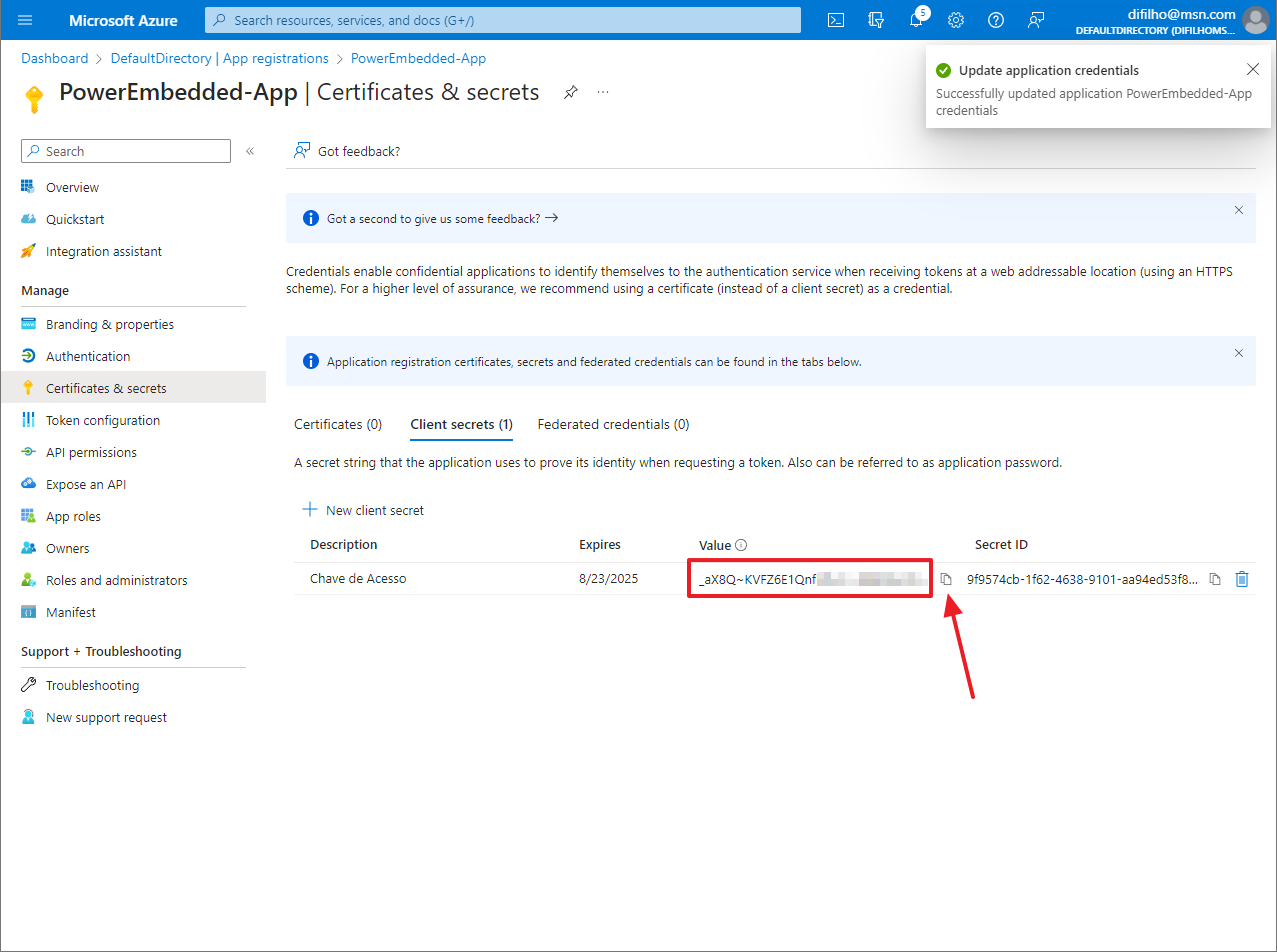
Now copy the generated “Value” field. There is a copy button next to this key.
Write down and keep this key safe, as this will be the ONLY time you will be able to see it. If you lose this key, it will not be possible to recover it: You will need to generate a new secret and update it in the system.
This value that I highlighted and you copied, you must paste into the field “Power BI Client Secret” on the Power Embedded configuration screen.
Sync Azure AD users and groups (Entra ID)
To integrate Power Embedded with Azure AD (Entra ID) and import users and groups.
On the same application registration screen, click on “API permissions” and then “Add a Permission”.
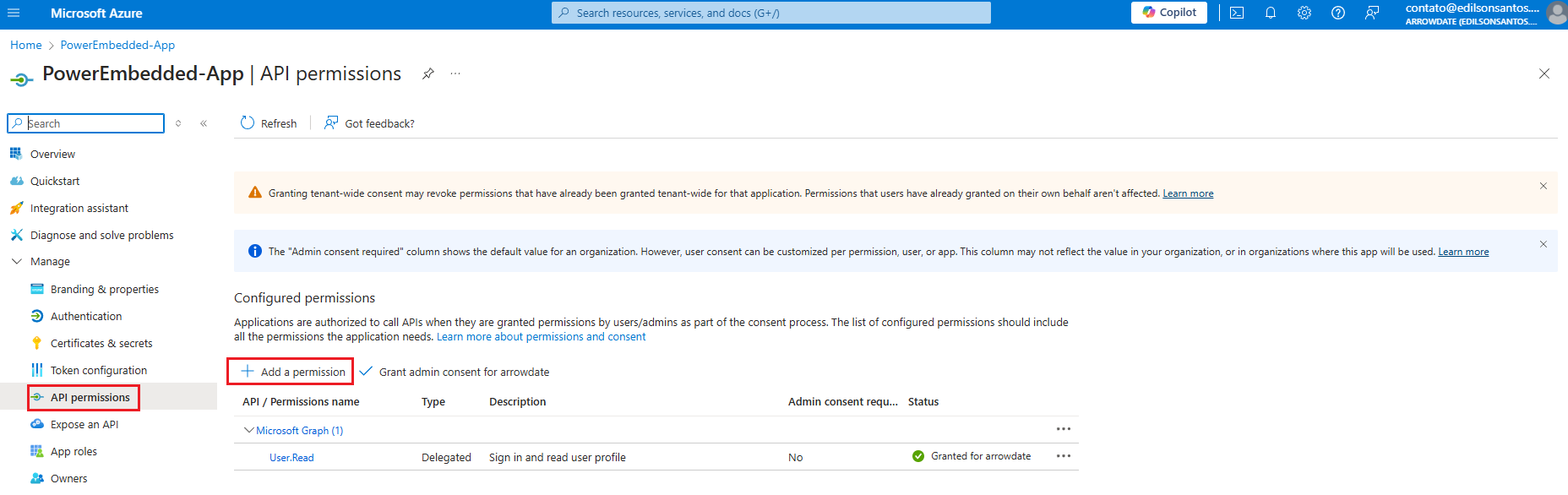
On the next screen select the “Microsoft Graph” option.
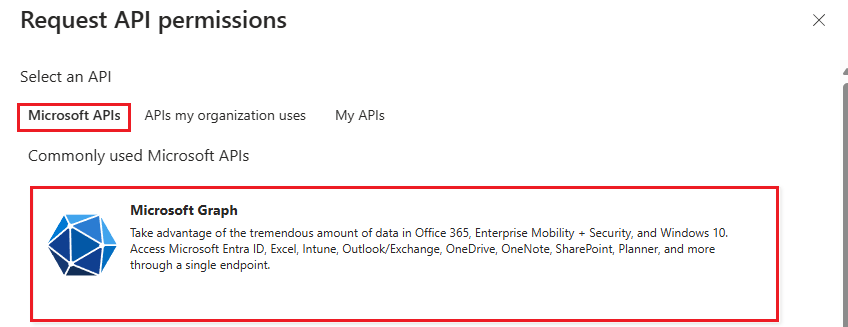
Then select the “Application permissions” option.
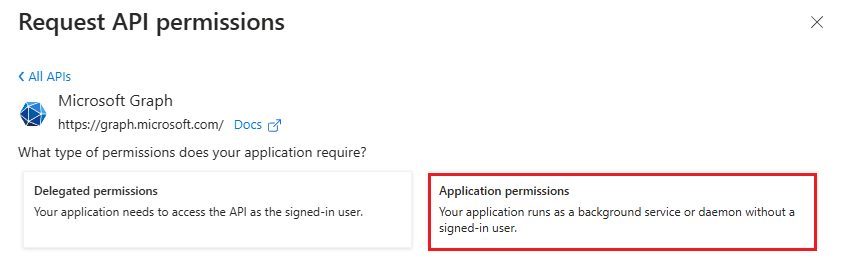
In the next tab, search for “Directory” and select the first option “Directory.Read.All” and click “Add permissions”.
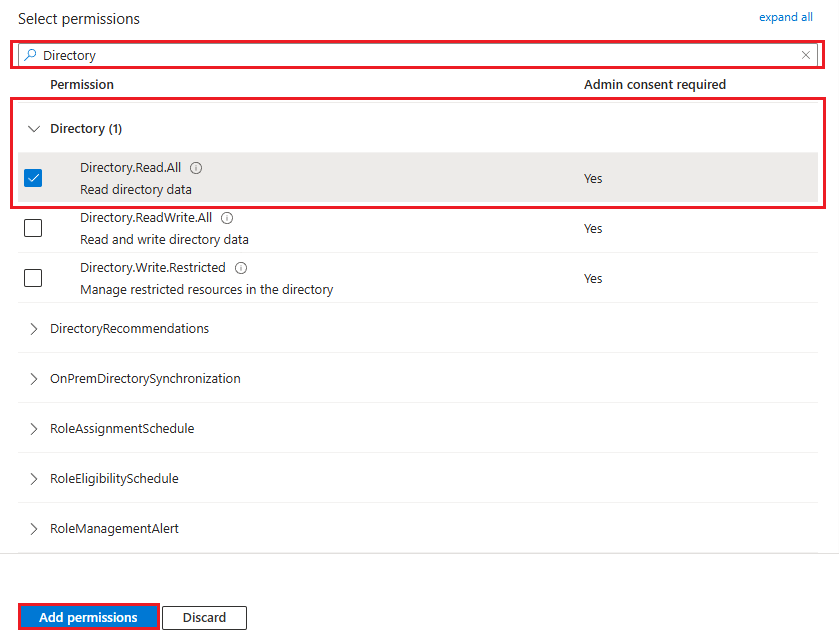
To finish, simply grant administrator consent by clicking on “Grant admin consent for”.
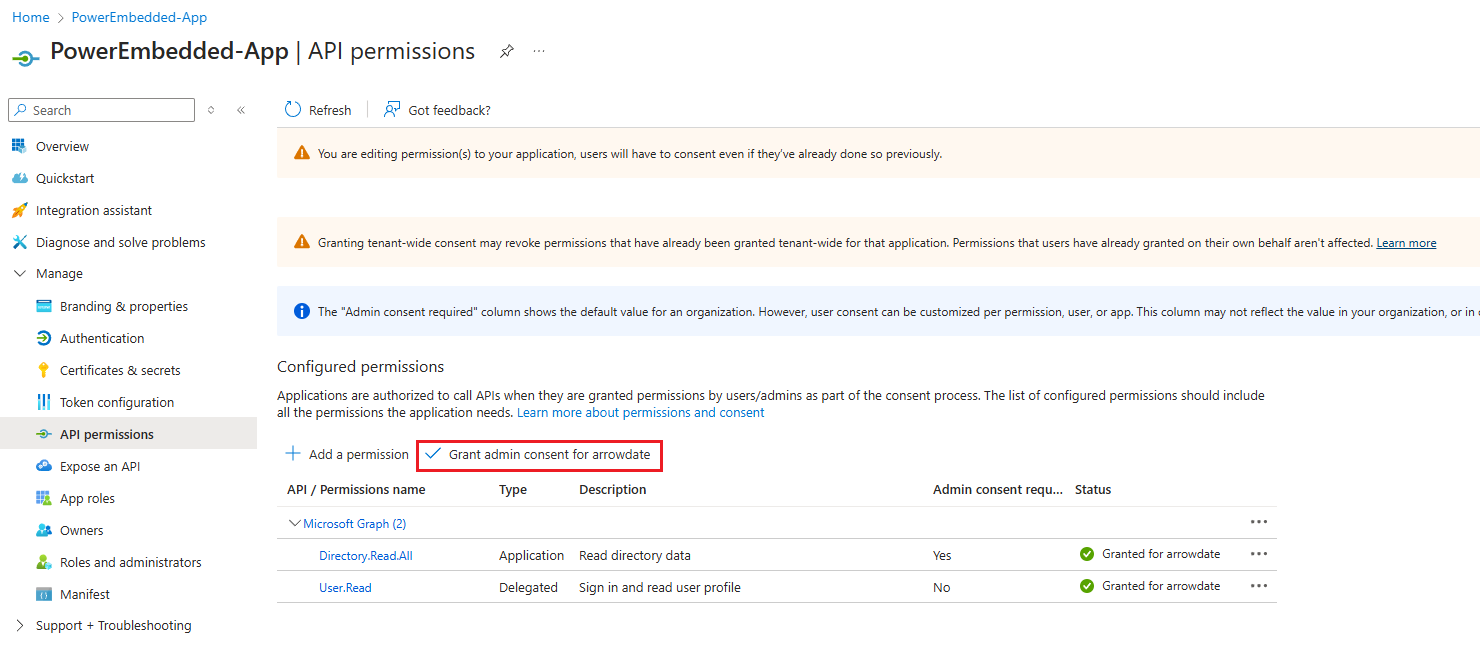
Done, when you complete the next steps you will be able to import users and groups from Azure AD (Entra ID) to Power Embedded.
Adding Power Embedded user to a new AD group
To grant permissions in the Power BI Admin Portal to the Service Principal you just created, it must be part of an Azure AD security group (Entra ID).
To do this, go to this link here and click on the “New group” button.
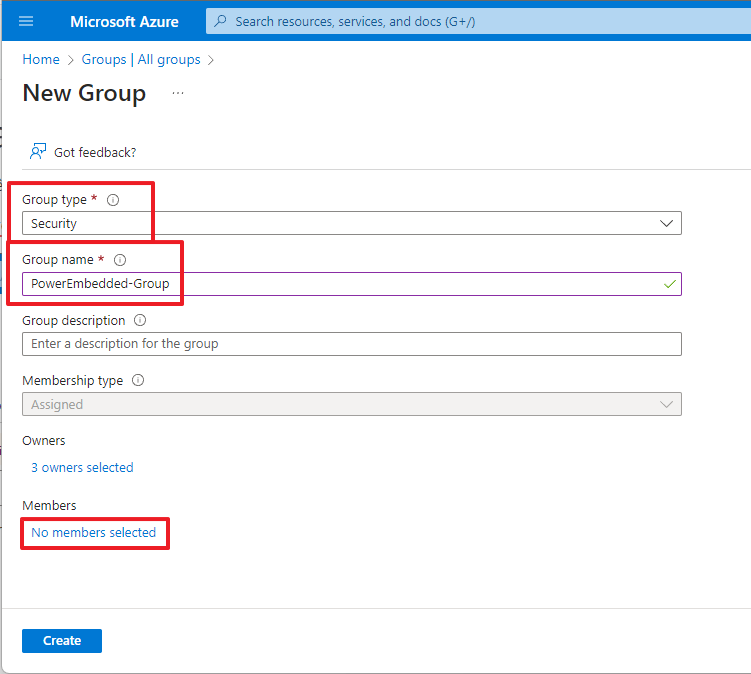
Select the “Security” option in the “Group type” field and enter a name of your choice for the group we are creating.
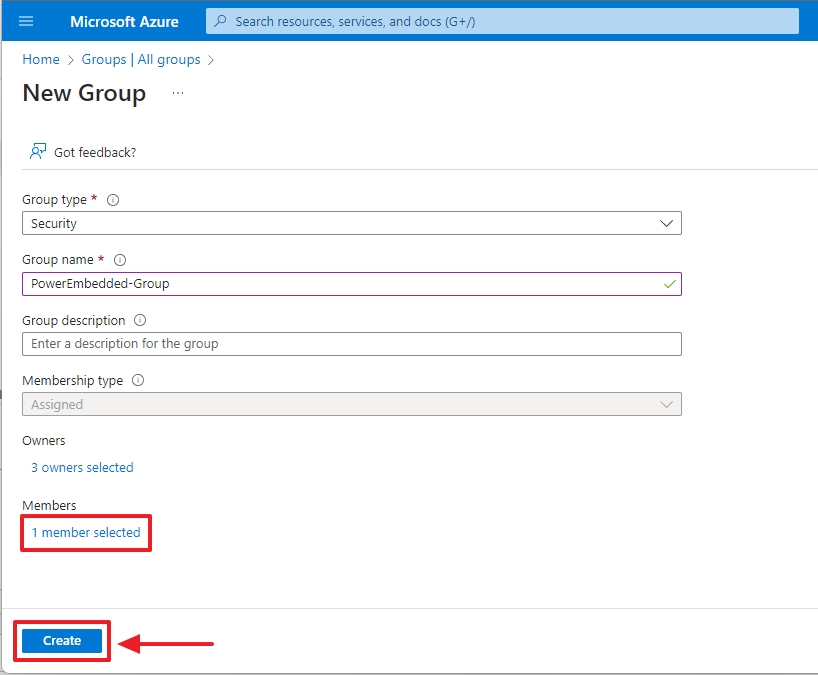
Click on the “Owners” link and add the people who will be responsible for Power Embedded.
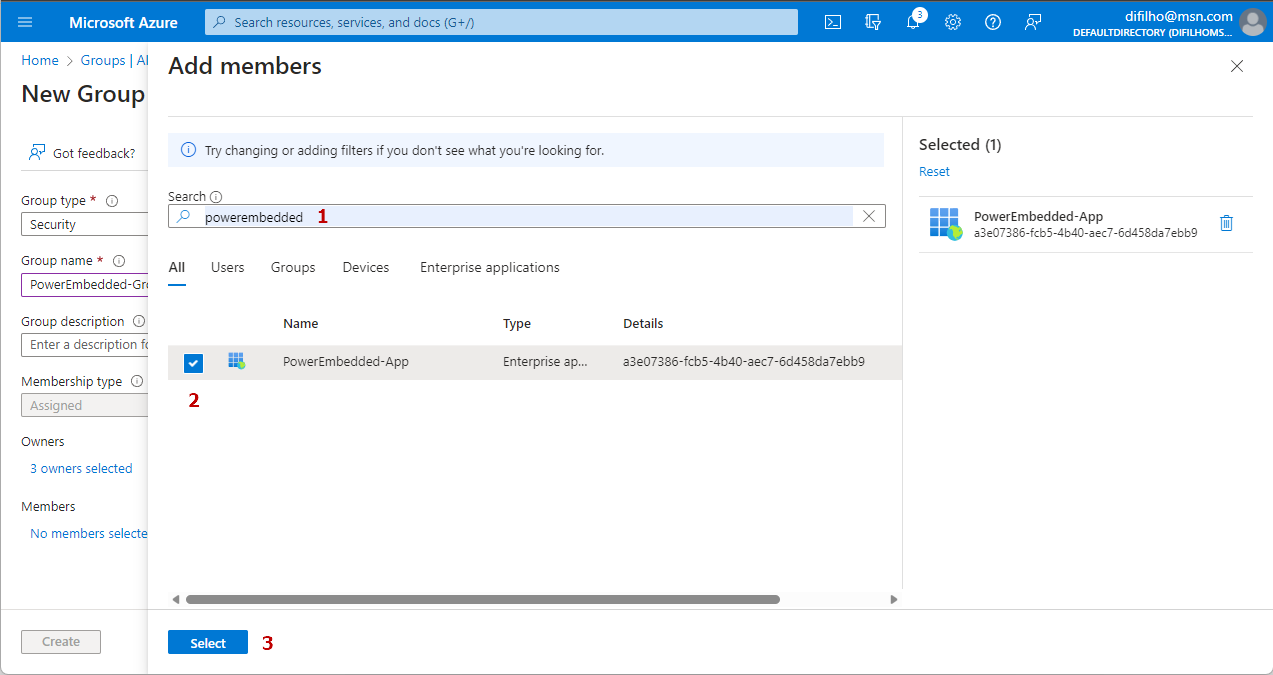
Click on the “No members selected” link in the “Members” category
In the screen that opens, enter the name of the Service Principal you created to filter. Select the Service Principal from the list and click the “Select” button at the bottom of the page.
Now that you have selected the member to add to this new group, click the “Create” button at the bottom of the page.
How to release the necessary permissions in the Power BI Admin Portal
Using a user with Power BI administrator permission, access this link here.
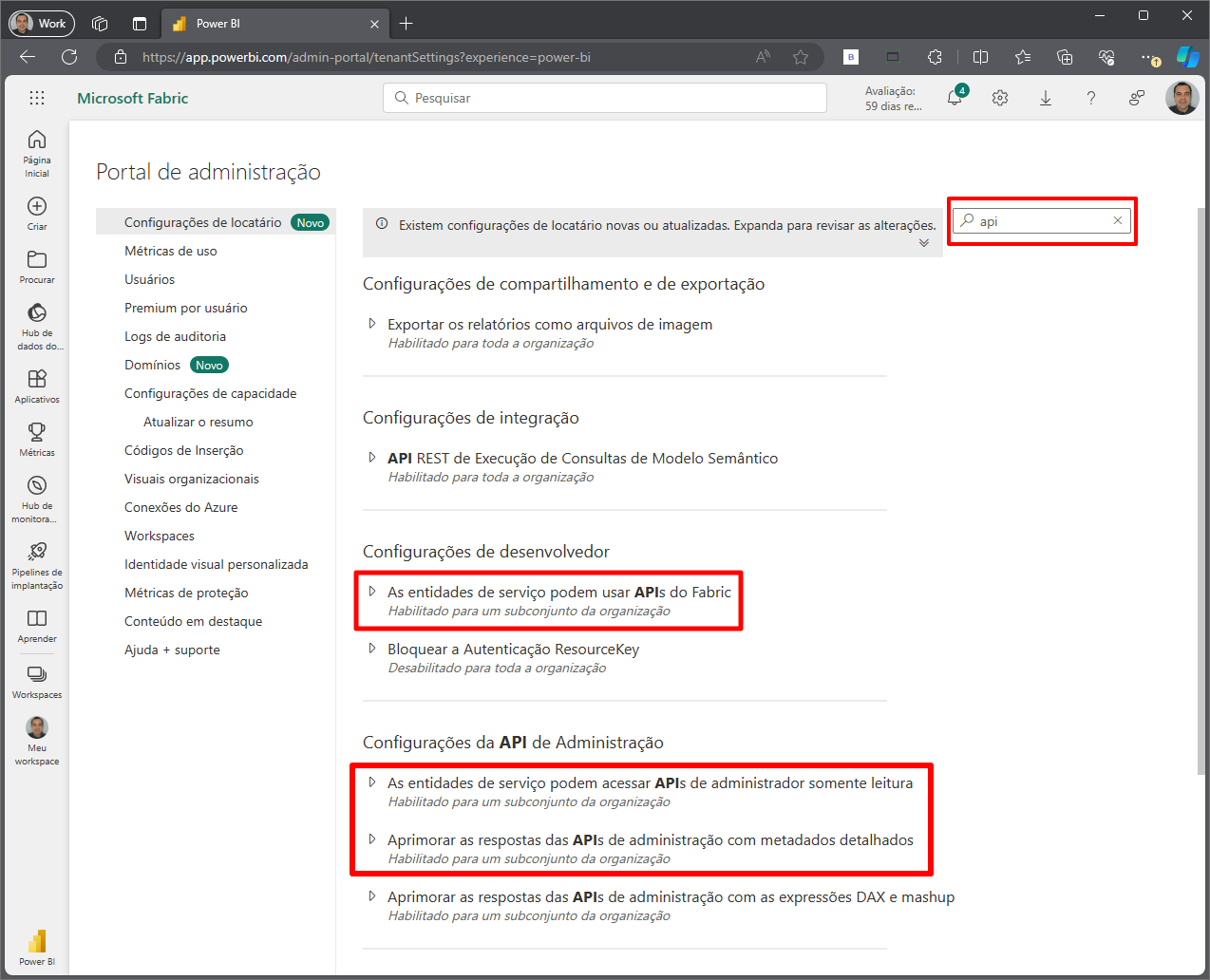
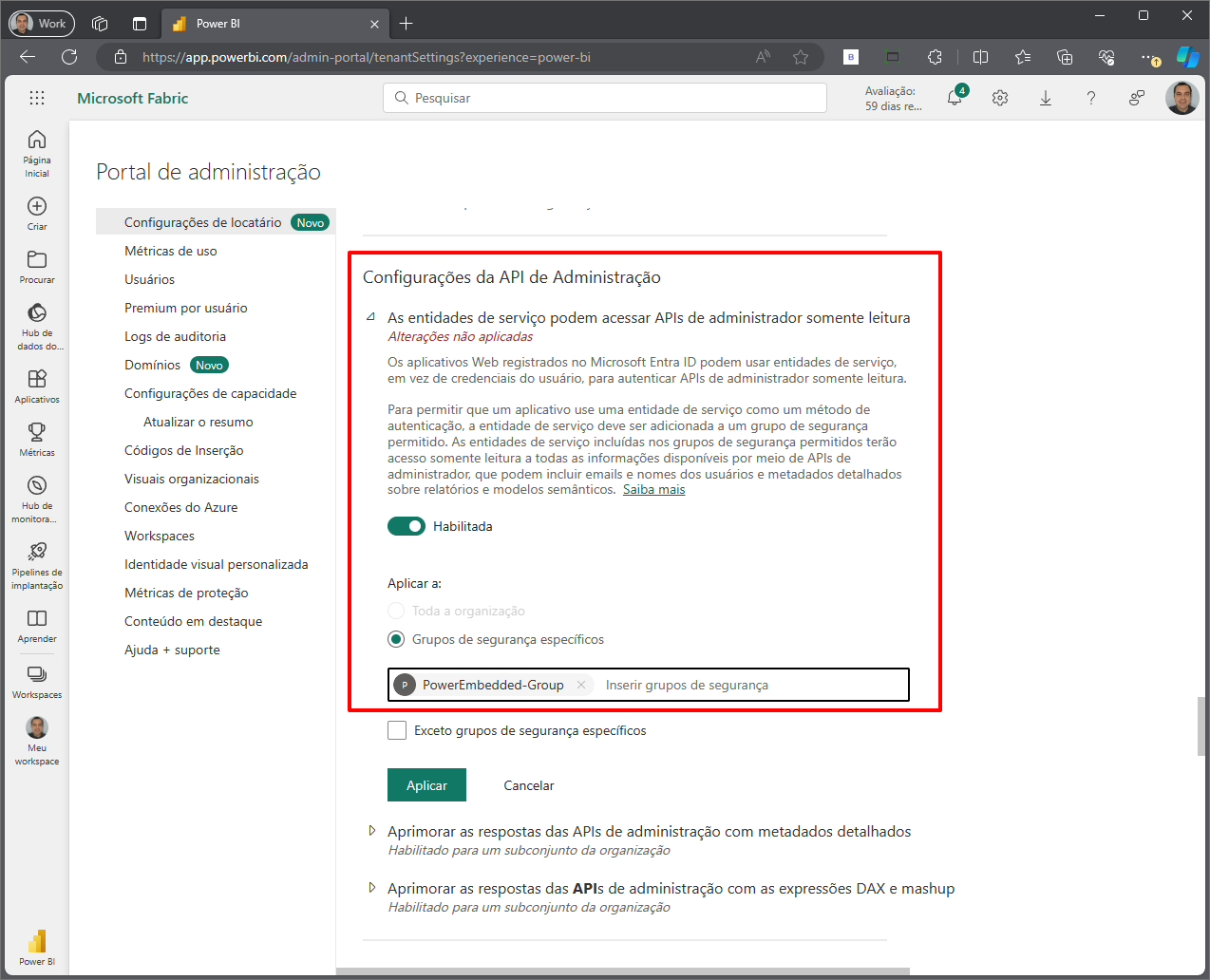
Scroll down until you find the “Developer Settings” section (or search for “api” in the search bar on the right)
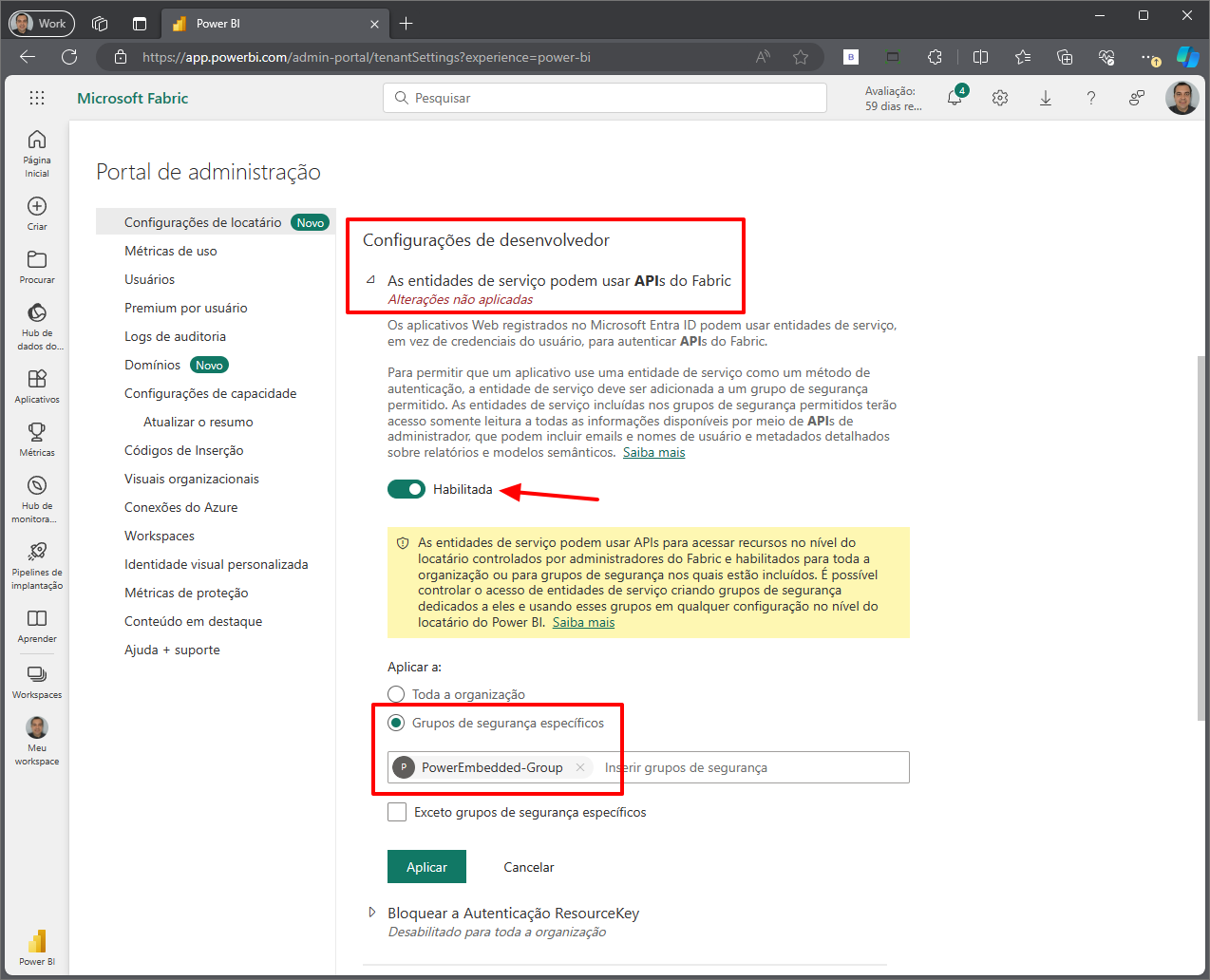
Check the option “Service principals can use Fabric APIs”.
For security reasons, check the option “Specify security groups” in the “Apply to:” section and select the security group we created at the beginning of this topic (in my case, “PowerEmbedded-Group”)
Click the “Apply” button.
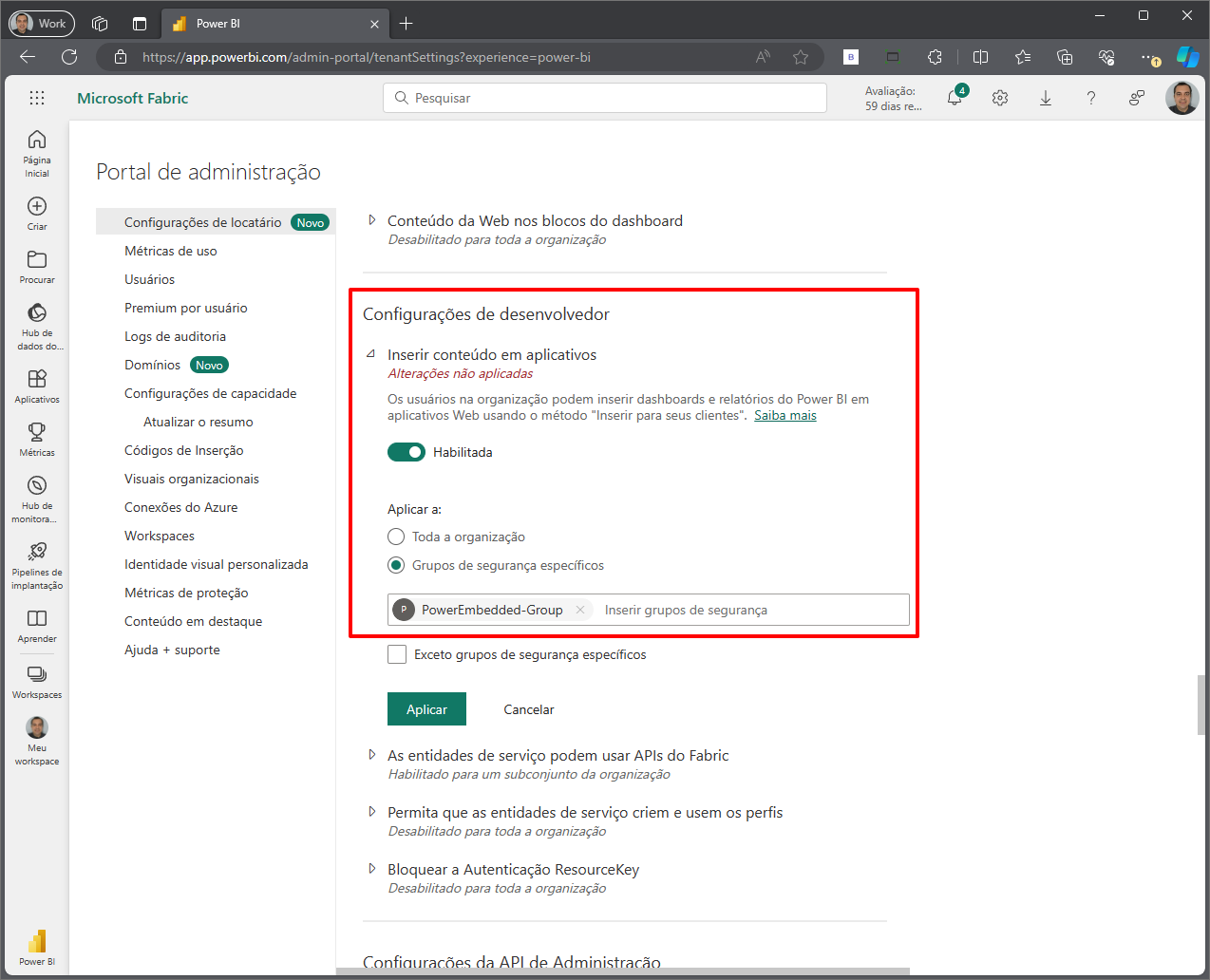
Scroll down a little further and repeat the same process for the item “Service principals can access read-only admin APIs” e “Enhance admin API responses with detailed metadata”, in the section “Admin API Settings”.
Atualize a página e agora a opção “Aprimorar as respostas das APIs de administração com as expressões DAX e mashup” vai ficar disponível para ser marcada. Repita o mesmo processo para essa permissão.
Still in the category “Developer Settings”, or by searching for “insert” in the search bar, select the option “Embed content into apps” and add the security group you created in the “Specific security groups” filter, in the “Apply to” option.
If this setting is already enabled and allowed for the entire organization, which is the Power BI default, you can leave it that way if the customer agrees. Changing this may cause problems in other processes if they are using something that requires this permission.
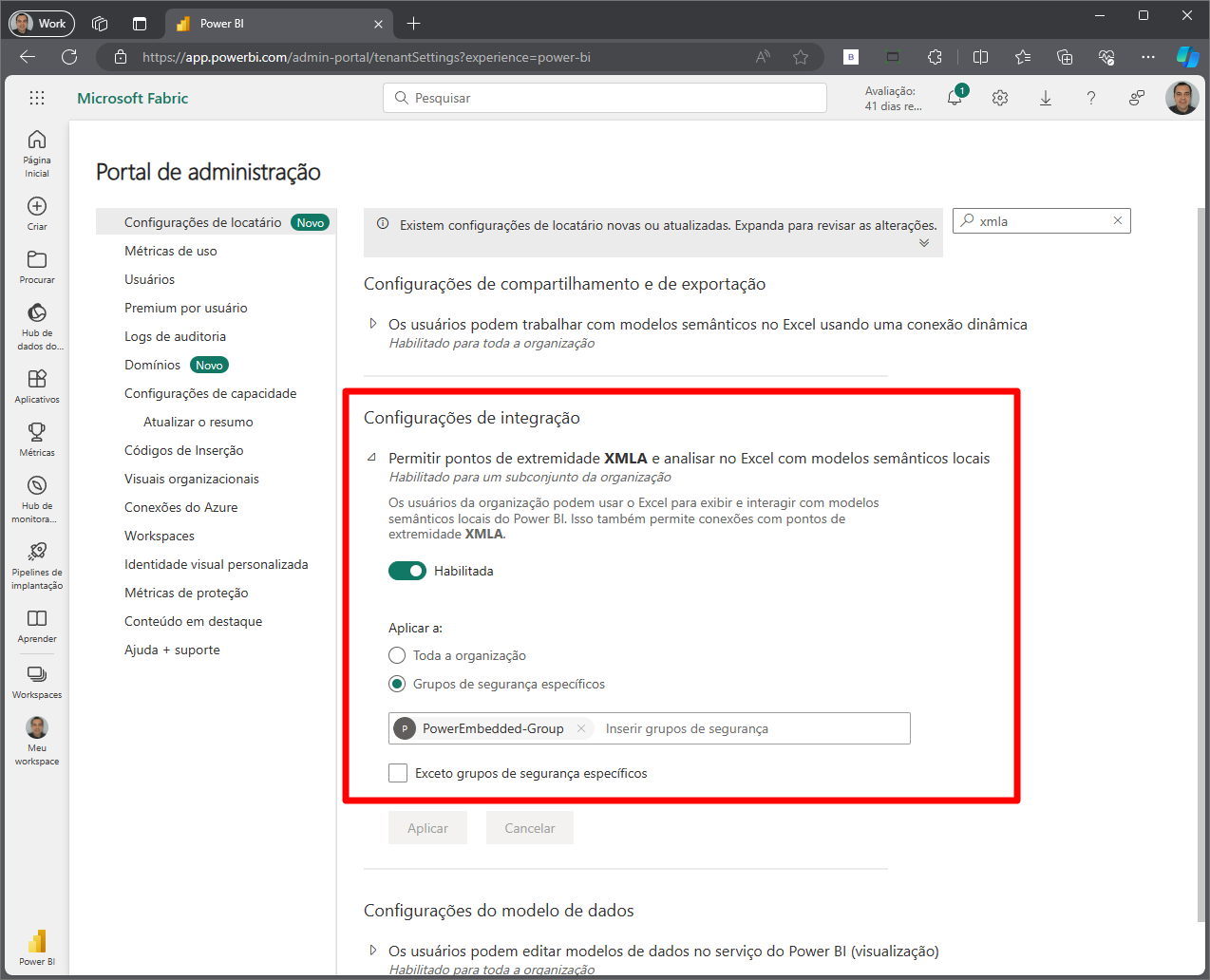
And finally, in the section “Integration Settings”, faça o mesmo processo para a configuração “Allow XMLA endpoints and Analyze in Excel with local semantic models”, which serves to allow the automatic listing of RLS roles.
If this setting is already enabled and allowed for the entire organization, which is the Power BI default, you can leave it that way if the customer agrees. Changing this may cause problems in other processes if they are using something that requires this permission.
Done! Now the Portal has access to your Power BI environment.
First access to the Administrative Portal
Access the administrative area of the Portal by accessing this link here, logged in with a user with permission to “Azure Global Administrator”.
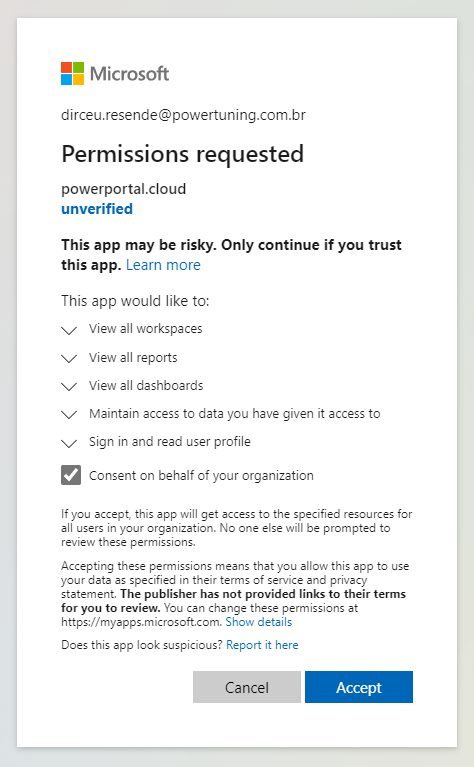
You will authenticate with your Microsoft account and once you finish logging in, you will see a permission request screen in your Azure AD.
Check the “Consent on behalf of your organization” option and click the “Accept” button.
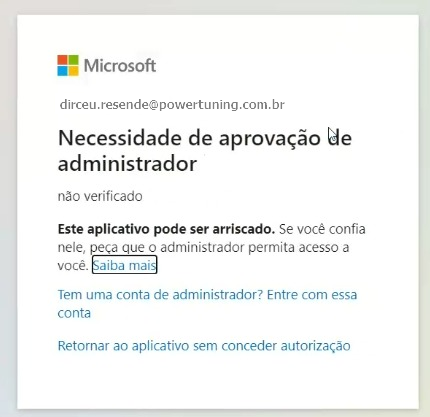
Did you forget to check the “Consent on behalf of your organization” option or did you install with a non-administrator account?
Click here to see how to manually release permissionIf you have accessed the administration portal using a user without the necessary permissions, the screen above may not appear for you, and the screen below may actually appear when you or another user tries to log in to the administration area.
If this happens, you will need to authorize the Power Embedded application (powerportal.cloud) on behalf of the organization, using a user with global permissions in Azure AD.
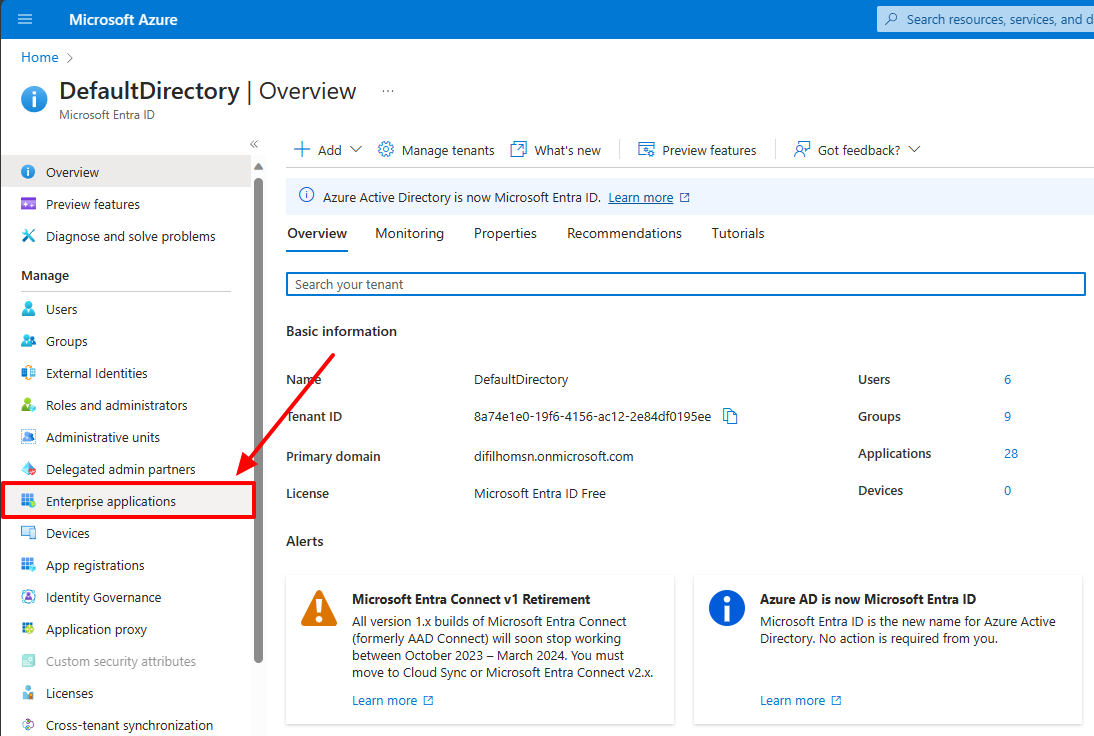
To do this, click on the link “Enterprise Applications” from Azure AD (Entrance ID)
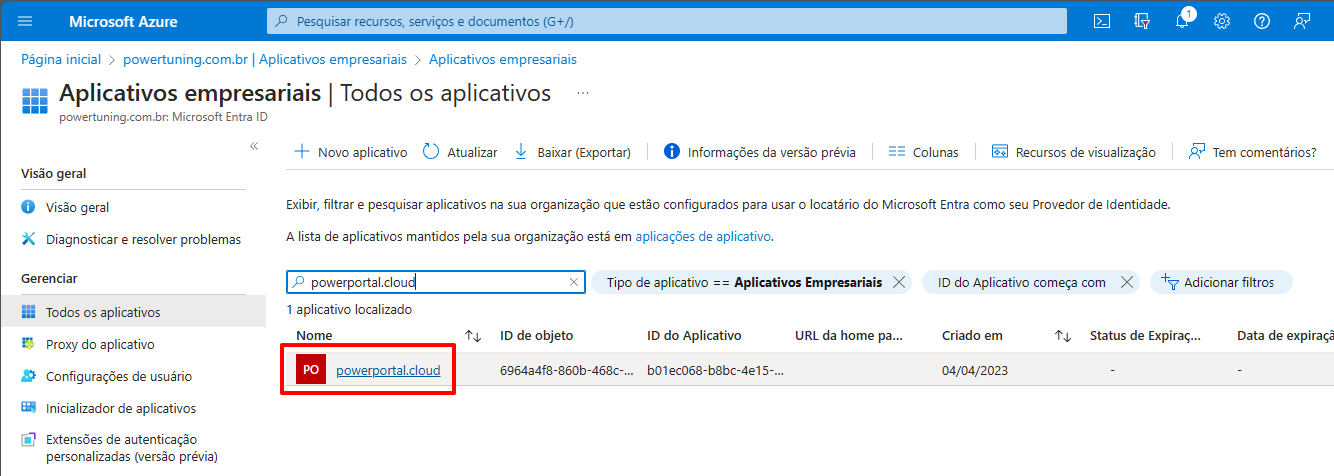
Locate and click on the “powerportal.cloud” application
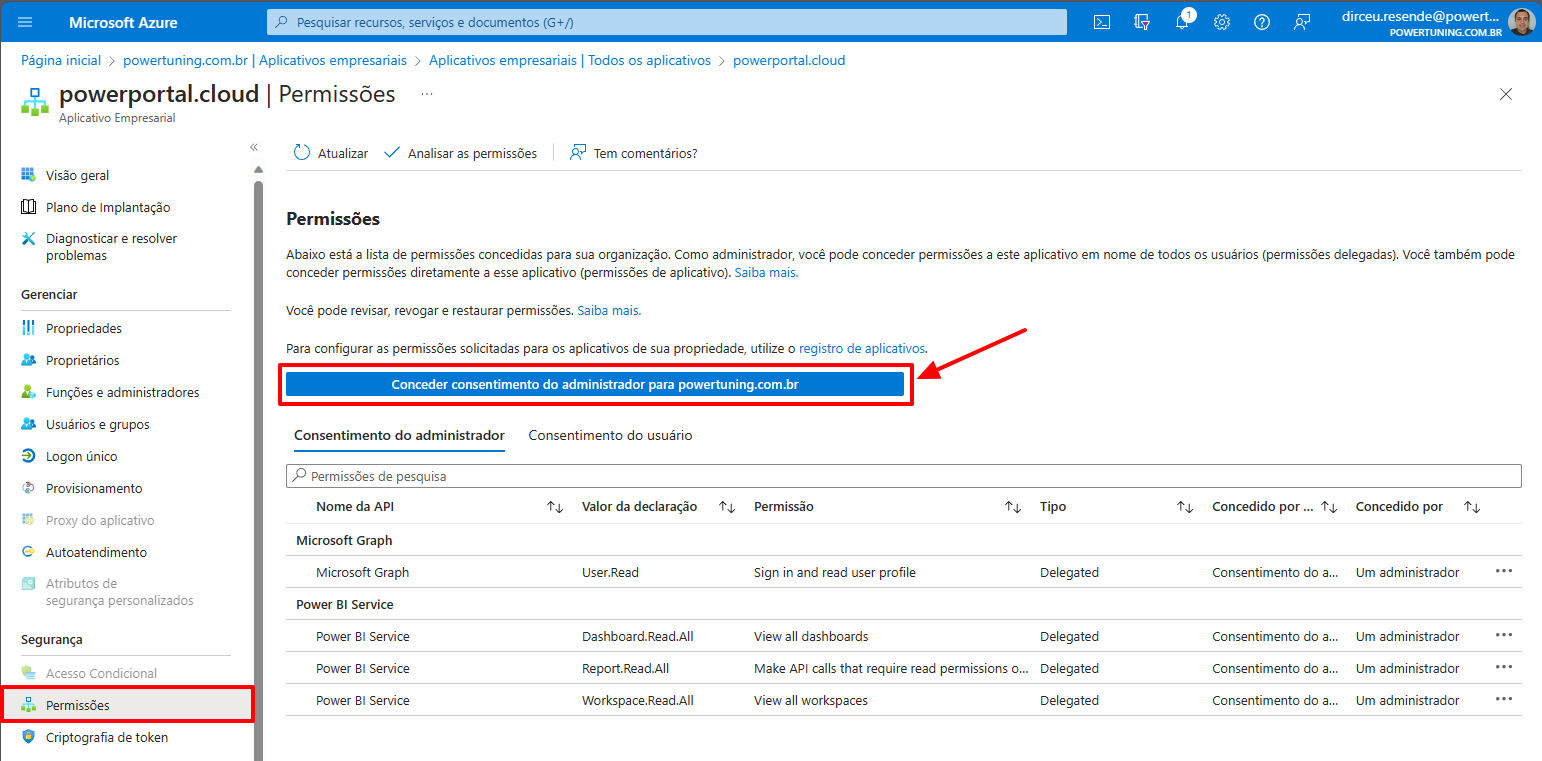
Click on the “Permission” menu in the left panel and then click on the “Grant admin consent for…” button and authorize the application.
After confirming the permissions, you will be directed to the system and must create the new organization.
On this screen, you can configure the following settings:
- Name: This is the name of your company. The system will retrieve the name registered in the Azure Tenant, but you can change it on this screen or later, through the system settings page.
- Power BI Client Id: This is the Service Principal ID that will be created to integrate Power Embedded with your Azure Active Directory (we will explain more about this below).
- Power BI Client Secret: It is the secret generated for the Principal Service (we will explain more about this below).
- Custom Domain: This is your company's domain (without www or https). This field will be used to create a personalized access URL to access reports (e.g. relatorios.suaempresa.com.br)
With the Client ID and Secret Value that you obtained at the beginning of the installation and wrote down in a notepad, we will now use them in the Power Embedded organization configuration screen:
Click on the “Create Organization” button and you can start using the Portal.
How to integrate Portal with Power BI Workspace?
In order to import Power BI reports into Power Embedded, you will need to do two things in the workspace:
- Activate the Fabric trial period (if you haven't already).
- Change Workspace capacity to Fabric capacity.
- Add the created Service Principal (Power Embedded user) as an administrator of the workspaces you want to import reports (can be more than 1).
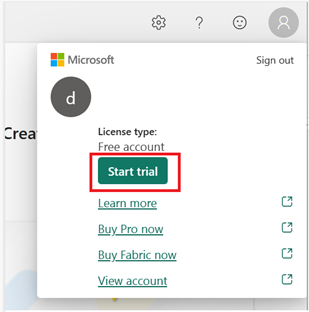
To activate your Fabric trial, click your photo in the Power BI menu
It is worth remembering that only 6 people in the organization can have started the Fabric trial, and once a person has already activated the trial, it is not possible to reallocate this capacity to another person.
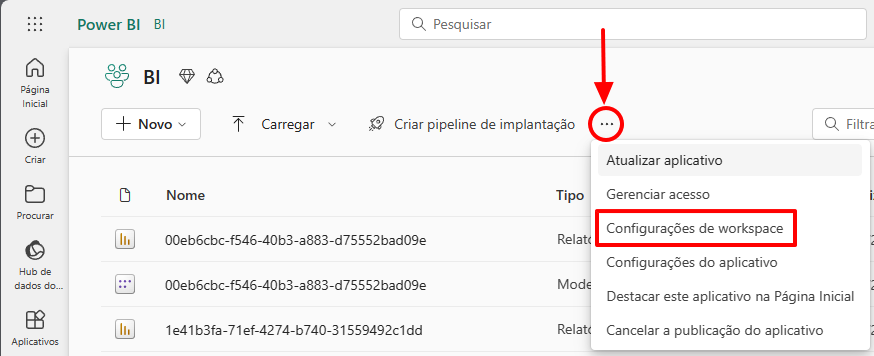
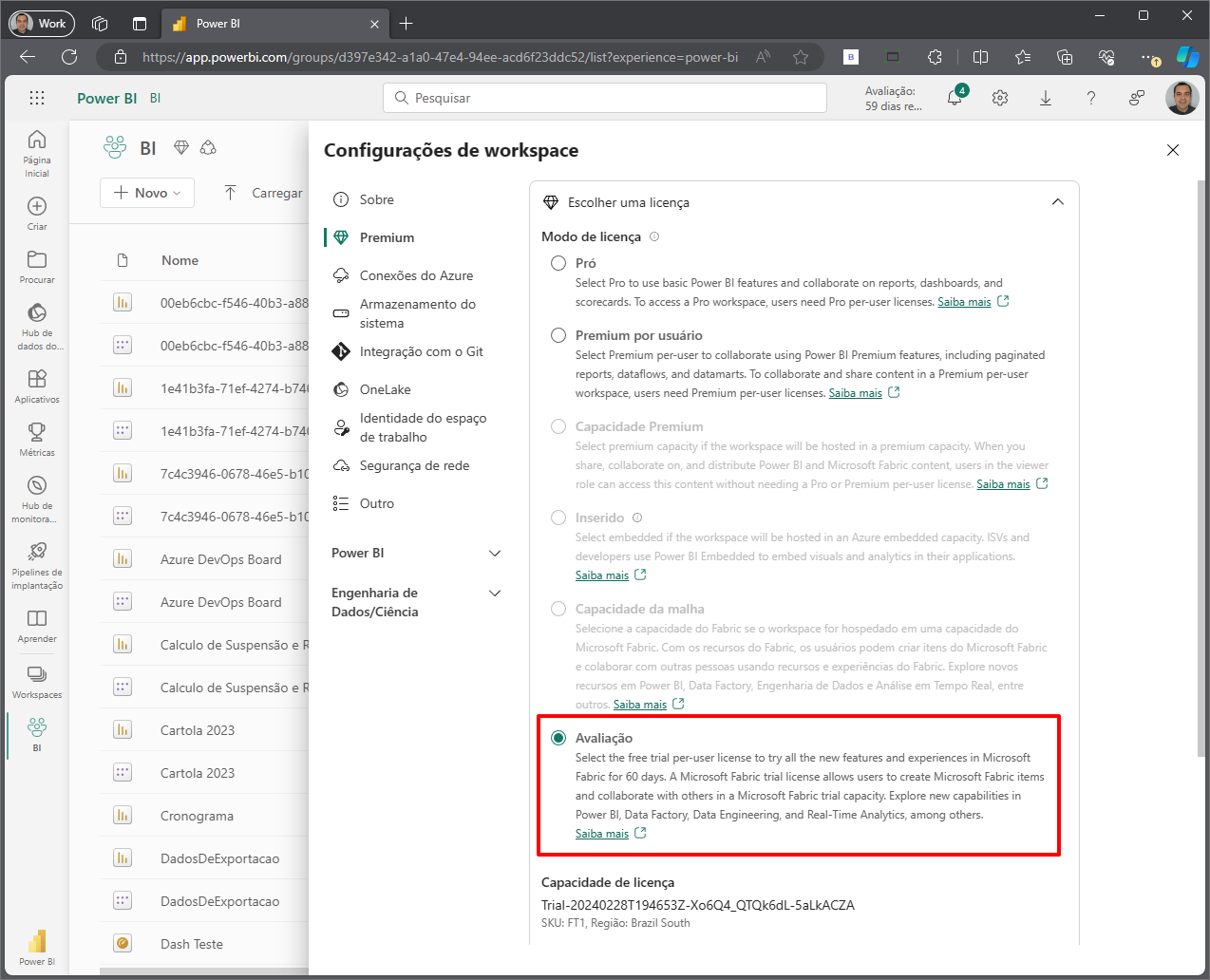
To change the Workspace capacity to Premium (Fabric) capacity, access the workspace, click on the 3 dots and select the “Workspace Settings” option
On the screen that opens, click on the “Premium” menu, then choose the “Embedded” license and in the “License mode” field, select the “Evaluation” feature.
Click on the “Apply” button below.
From this point on, this workspace is now in Fabric Premium capacity. If you pause this feature, the Workspace will be inaccessible, even if you use a Pro account and access it directly through the portal.
The last step now is to add the Service Principal user to the Workspace.
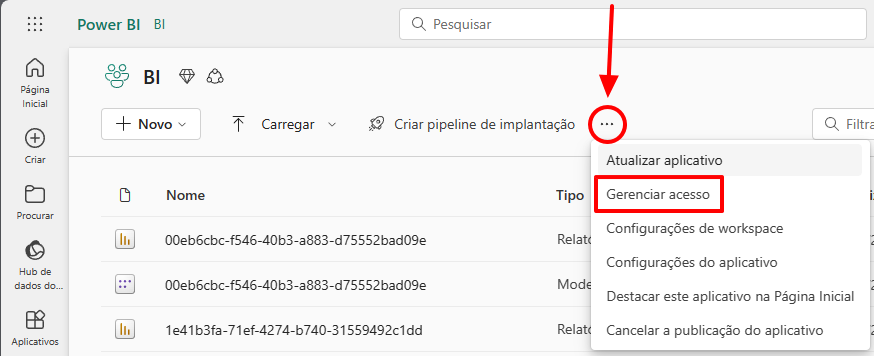
To add the created Service Principal as an administrator of a workspace, access the workspace, click on the 3 dots and select the “Manage access” option.
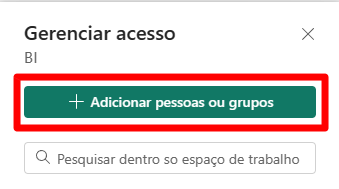
Click the “+ Add people or groups” button.
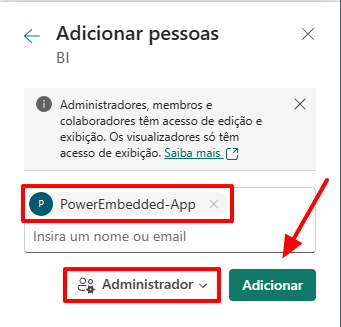
Search for the name of the application that was created previously (PowerEmbedded-App) and remember to change the access level to “Administrator”. After that, click the “Add” button.
Done! Now Power Embedded has access to this workspace. Repeat this for all the Workspaces you want to import reports from.